Ledger Live Access: The True Meaning of "Login"
The Secure, Device-Based Gateway to Your Decentralized Assets
Ledger Live is not just an application; it is the essential interface to the world’s most secure digital asset management system, anchored by your Ledger hardware wallet. Unlike traditional platforms that rely on vulnerable username/password combinations, **Ledger Live's "login" process is fundamentally different and inherently superior**, aligning with the core principles of self-custody and high-grade security. This comprehensive guide details the mechanism, security features, and best practices for accessing and managing your crypto portfolio with the highest level of confidence.
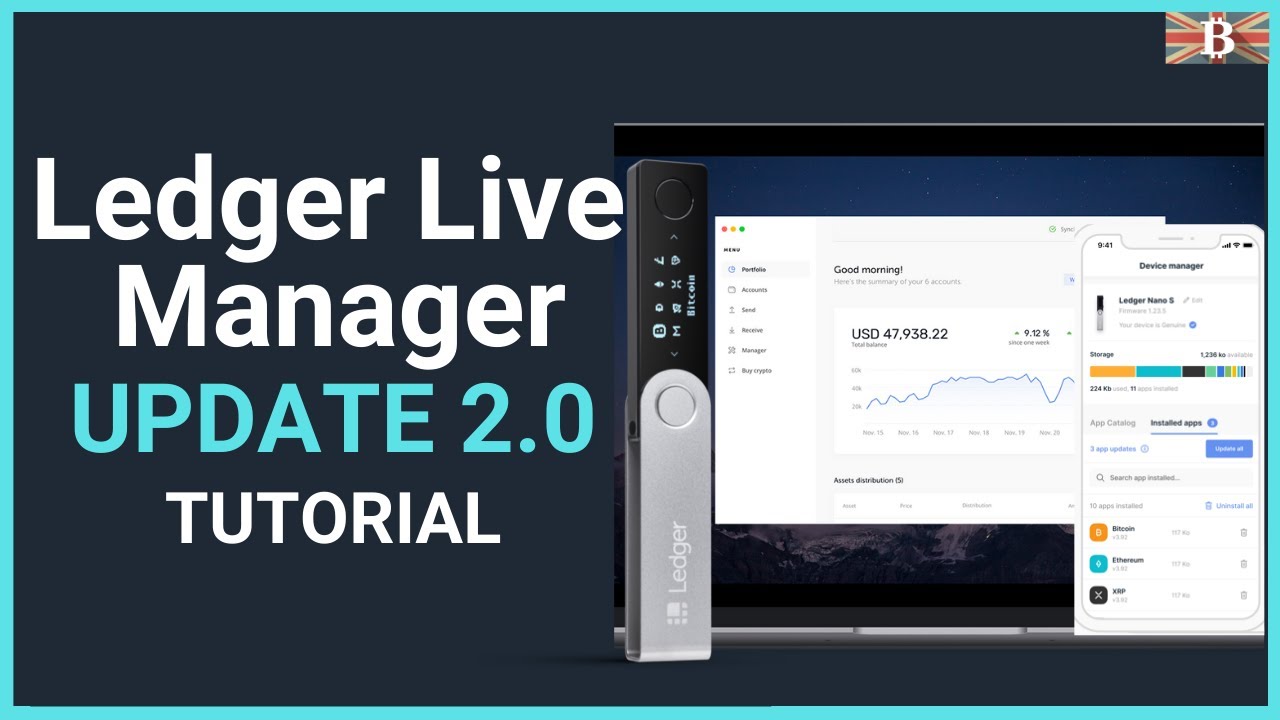
The Security Paradigm Shift: No Password Required
The single most crucial concept to grasp about Ledger Live is that it does **not** rely on a cloud-based account, nor does it require a password that can be phished, leaked, or brute-forced. Your assets are never stored in the application or on your computer; they remain secured by the **Private Keys** isolated within the Secure Element chip of your physical Ledger device (Nano S, Nano X, or Stax). Therefore, the act of "logging in" is simply the process of **connecting and unlocking your physical device**.
This **refined site** experience emphasizes the device-first approach. When you launch the Ledger Live application on your desktop or mobile, the app merely acts as a read-only viewer for your public addresses. To perform any actions—to send funds, swap assets, or modify settings—you must physically authenticate. This design ensures that even if your computer were compromised with malware, the attacker could not authorize a transaction without physical access to your device and knowledge of your **PIN code**. This multi-layered defense is what defines the Ledger security model.
Step-by-Step Guide to Accessing Ledger Live
Step 1: Launch and Connect
Open the Ledger Live application. Connect your Ledger hardware wallet to your computer via a USB cable (or via Bluetooth for the Ledger Nano X/Stax). The application will detect the connected device.
Step 2: Enter PIN on Device
Your Ledger device screen will prompt you to **Enter PIN**. You must enter your confidential PIN directly on the device itself—never on your computer keyboard. This critical action unlocks the Secure Element.
Step 3: Sync and Manage
Once the correct PIN is entered and confirmed on the device, the hardware wallet communicates with Ledger Live, verifying that the private keys are available for signing transactions. Ledger Live will then sync your portfolio balance, enabling you to view and manage your accounts. No data leaves your device during this process; the app is simply reading the public ledger (blockchain).
The Pillars of Security: Beyond the PIN
Achieving a truly **high-quality content** experience requires a deep understanding of the security mechanisms that underpin the platform. The access mechanism is rooted in three key pillars, far surpassing the security of conventional logins:
- The Secure Element (SE): The CC EAL5+ certified chip on the Ledger device that physically isolates your private keys, making them impossible to extract.
- The PIN Code: A four-to-eight-digit code entered on the device. It protects against unauthorized physical access to your wallet. Three incorrect attempts will trigger the device to wipe itself, protecting your assets (which can be recovered using your recovery phrase).
- The 24-Word Recovery Phrase: This is your master backup. It is the only thing that can restore your private keys to a new device. It must be stored offline, physically, and securely. **Never, under any circumstances, type this phrase into a computer or Ledger Live.**
Troubleshooting Common Access Issues
If you encounter issues during the connection or synchronization process, consider these common troubleshooting steps. A smooth, **refined site** experience depends on proper device and software maintenance:
- **"Device Disconnected" Error:** Ensure you are using the original USB cable and that the cable is fully seated in both the device and the computer port. Try switching to a different USB port.
- **Ledger Live Update:** Always keep your Ledger Live application and your device's firmware up-to-date. Outdated versions may cause connection or syncing errors.
- **Close Competing Software:** Other cryptocurrency wallets or applications that try to communicate with your Ledger device (like MetaMask or crypto exchanges) must be closed before launching Ledger Live.
- **Bluetooth (Nano X):** If using Bluetooth, ensure the device is charged and properly paired with your mobile device through the Ledger Live application settings.
In summary, the Ledger Live "login" is a testament to secure self-custody. It is an **active, physical authentication** requiring possession of the hardware and knowledge of the PIN, making it vastly more secure than a simple password entry. This process ensures that you, and only you, maintain absolute control over your digital wealth.